Zone-H 는 크래킹당한 사이트들을 알려주는 사이트이기도 합니다.
그 사이트가 디페이스 되는 바람에 참 재미있는 일이 벌어졌네요 ^_^
Zone-H.org 에서 가지고 온 분석본입니다.
As you may have noticed, Zone-H got defaced in the night between Dec 21st and Dec 22nd. This was an elaborated attack that was possible (as most of the past Zone-H incidents), starting with the exploitation of the human factor. We are pleased to post this explanation as it is a very good example on how your security can be jeopardized by bugs, and ones (Hotmail) apparently not related to the system you are using.
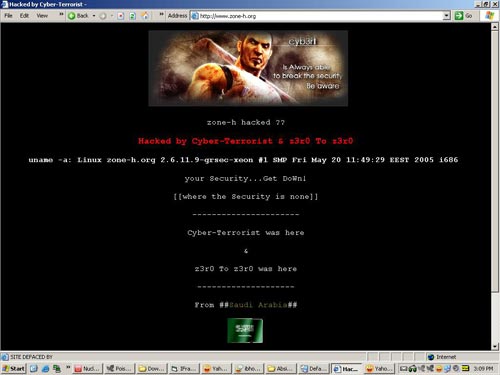
그 사이트가 디페이스 되는 바람에 참 재미있는 일이 벌어졌네요 ^_^
Zone-H.org 에서 가지고 온 분석본입니다.
As you may have noticed, Zone-H got defaced in the night between Dec 21st and Dec 22nd. This was an elaborated attack that was possible (as most of the past Zone-H incidents), starting with the exploitation of the human factor. We are pleased to post this explanation as it is a very good example on how your security can be jeopardized by bugs, and ones (Hotmail) apparently not related to the system you are using.
The funny part is that the incident happened yesterday night,
exactly when all Zone-H board members where around a table for the
x-mas dinner discussing about an hypotethical Zone-H incident and
backup policies.
Everything started on Dec. 17th...
Dec 17th - step one: The attacker decided to target one of our
Zone-H contributors (no names, let's call him TARGET which, by the way,
had only limited privileges on our Joomla based platform) by sending a
"I forgot my password" reset request, to the Zone-h server running a
CMS, Joomla knowing that it would send to the TARGET email address, a
Hotmail account, a new password.
Dec 17th - step two: The attacker took advantage of the recent
http://lists.grok.org.uk/pipermail/full-disclosure/2006-August/048645.html
( The Hotmail XSS bug ) to get the TARGET's Homail session cookie. By
accessing his email the attacker obtained the newly generated Joomla
frontend password.
Dec 17th - step three: By obtaining the TARGET's frontend Joomla
password the attacker gained the same privileges as other Zone-H
contributors that allowed them to upload a news article with some
pictures (but not to publish it!). He used such privileges to upload
news containing an image file that resembled a defacement and submitted
it to our defacement mirror. But this didn't work as the attacker
didn't realize that the defacement page was visible only to those
having administrative rights, not even our mirror robot could take a
snapshot of it. Having no mirror of that pseudo-defacement and being it
visible only to the administrator we decided not to publish the entry
in our database.
We disabled the TARGET’s Zone-H front-end administrative account.
Dec 18th: - step four: The attacker realized that the image file
he uploaded and used in his previous defacement attempt was still
present in the zone-h image folder, therefore he simply notified the
Zone-h mirror robot with a url like:
www.zone-h.org/imagefolder/imagename. The mirror robot liked it and
accepted it. Even though that image would have never appeared by
itself, the mirror robot took the snapshot therefore we decided to
publish it in our archive.
After all, the attacker managed to craft an attack against one of
the Zone-H staff members and had uploaded a file in our server finding
finally the way to make it visible.
Fair enough, defacement + star.
Dec 21th: step five: We thought the attack was finished but this
time the "real" defacement arrived, by the same attacker. Apparently
during the first defacement he uploaded not only the image file used in
the first defacement attempt but also a php shell (shame on us we
didn't find it, but hey... it's x-mas time, we are all busy with
shopping down here...). The attacker didn't know though how to use the
shell, as
Zone-H security policies didn't allow to execute it directly or
from within the defacement mirror frame. During Dec. 17th-18th the
attacker had a limited timeframe to access the Zone-H administrative
front-end during which he realized what components our Joomla
installation was integrated with in the administrative front-end (a mix
of self-written modules and standard modules). One of the modules was
the JCE editor that contained a file inclusion flaw where input passed
to the "plugin" and "file" parameters within jce.php was not properly
verified before being used to include files.
http://secunia.com/advisories/23160/
He understood now that he could finally run the previously uploaded PHP shell, and here we see that request:
- - [21/Dec/2006:23:23:15 +0200] "GET
/index2.php?act=img&img=ext_cache_94afbfb2f291e0bf253fcf222e9d238e_87b12a3d14f4b97bc1b3cb0ea59fc67a
HTTP/1.0" 404 454
"http://www.zone-h.org/index2.php?option=com_jce&no_html=1&task=plugin&plugin=..<>/<...<///..<////..<////..<////..<////images/stories/food/x
&file=defi1_eng.php.wmv&act=ls&d=/var/www/cache/&sort=0a"
"Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.0.3705)"
and shortly after:
- - [21/Dec/2006:23:23:59 +0200] "GET
/index2.php?option=com_jce&no_html=1&task=plugin&plugin=..<>/<...<///..<////..<////..<////..<////images/stories/food/x&file=defi1_eng.php.wmv
&act=ls&d=/var/www/cache/cacha/&sort=0a
HTTP/1.0" 200 3411 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.0.3705)"
212.138.64.176 - - [21/Dec/2006:23:25:03 +0200] "GET /cache/cacha/020.php
HTTP/1.0" 200 4512 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.0.3705)"
Dec 21th: step six: The attacker, by exploiting the local file
inclusion in jce component, used the first (nearly useless) php shell
to create a new directory (/var/www/cache/cacha), to create a new shell
(020.php) and to create a custom .htaccess to disable mod_security in
that specific directory.
Dec 21th: step seven: The attacker used the brand new php shell,
without restrictions as mod_security has been disabled, to modify the
configuration.php file and insert the defacement HTML page
- - [22/Dec/2006:01:05:15 +0200] "POST
/cache/cacha/020.php?act=f&f=configuration.php&ft=edit&d=%2Fvar%2Fwww%2F
HTTP/1.0" 200 4781
"http://www.zone-h.org/cache/cacha/020.php?act=f&f=configuration.php&ft=edit&d=%2Fvar%2Fwww%2F"
"Mozilla/5.0 (Windows; U; Windows NT 5.1; ar; rv:1.8.0.9) Gecko/20061206
Firefox/1.5.0.9"
Oh well, nothing to say! This time we got it for real. A long time
has passed since Zone-H got defaced by means of real hacking (2002),
all other times had been by means of stolen passwords (social
engineering against one of our many, many, many contributors) and
by means of privilege escalation from within the administrative login,
done by one of our first (stupid) Zone-H staff member.
In a short recap, our faults were:
1) Having a staff member who was not wise enough to recognize a Hotmail XSS attack.
2) Not finding the uploaded, but useless at that time, php shell. Zone-H contains 80 gigs of files, but this no excuse.
3) Not acknowledging in time the JCE component advisory (and we
all make our living by reading tons of advisories every day...)
Our non fault was: using an open source CMS such Joomla. All CMSs
contain bugs and even assuming you had enough time to code your own CMS
(have you any idea how long it would take?) it would probably still be
vulnerable, as was vulnerable the first, self-written Zone-H CMS
(defacers never realized how to exploit the old Zone-H bugs, but we had
a couple of serious ones). For the sake of the truth, this is my
personal opinion while other staff members have always showed concerns
in implementing an open source CMS.
As a second gift from Santa, we received also a good dose of ddos
from people who didn't want to see a defaced zone-h online (why not!?!
The whole Internet is unsecure, it's Zone-H point to show it, after
all...)
Okay, that's all from Zone-H today. We wish you a merry X-mas
(also to the attacker, he managed to craft a very elaborated attack,
congratulation to him, we all hope he would put his skills into legit
activities rather than into defacing).
Ho-Ho-Ho... Meeerry Christmas...
PS: the incident is not in the Zone-H archive because Zone-H
policy is not to accept notification on multiple incidents happened to
the same server within a 6 month timeframe and we published the
previous Zone-H pseudo-defacement three days before. But you can still
find the mirror for the forum.zone-h.org (/net/com) as it was also
notified for those domains.
You might also notice a slowdown in publishing self-written news
during the next 2 weeks, as most of the staff took vacation. We also
would like to see an exception this year as x-mas time is usually the
time where the defacers are most active.
Why don't you use this time to take a REAL vacation, away from the
keyboard and away from the legal troubles defacements can bring along?
Real life (and hot chicks are out waiting for you...)
Special thanks to the great Siegfried (Kevin Fernandez) for the forensic analysis.

댓글,
